Microsoft Sysmon Data
Sysmon Overview
Sysmon, a component of Microsoft’s Sysinternals suite of Windows utilities, is a very powerful host-level tool that can assist in detecting advanced threats on a network by providing intricate host-operation details in real-time. In contrast to common Antivirus/Host-Based Intrusion-detection (HIDS) solutions, Sysmon performs deep monitoring on system activity and logs high-confidence indicators on advanced attacks.
This is a fantastic way to collect detailed information about your Windows endpoints in Splunk. Sysmon is free of charge, installs painlessly on many variants of Windows, and integrates well with Splunk deployments. In fact, Mark Russinovich (Sysmon’s author) has spoken about Sysmon at the past two RSA conferences and showcases Splunk as an excellent mechanism for the collection and analysis of Sysmon data.
App Installation
| App | Search Head | Indexer | Heavy Forwarder | UF / Deployment Server | Additional Details |
|---|---|---|---|---|---|
| Sysmon Deploy Add-on for Cyences App | - | - | - | Required (only for Windows) | Installation and Configuration |
| Splunk Add-on for Sysmon | Required | - | Required | - | Installation and Configuration Guide |
Note : Create an index named epintel or update the cs_sysmon macro definition from Cyences app configuration page (Cyences Settings > Cyences App Configuration > Products Setup).
Sysmon Deploy Options
User would have two option to install and upgrade Sysmon on their environment.
- Use Sysmon Deploy App mentioned above and install/upgrade Sysmon as well as maintain Sysmon configuration
- Use other automation or manual approach to maintain Sysmon and its configuration outside Splunk configuration management
1. Use Sysmon Deploy App - Deployed via Deployment Server (DS)
NOTE - In order for this App to install Sysmon and maintain its configuration, Splunk UF must be running as Windows Local Account. But as of Splunk version 9.x.y Splunk UF installs by default with service account, so user needs to manually change it once on all Windows servers. * This can be done from Services > Splunk Forwarder Service > Properties > Log On * And Change it to Local System account * 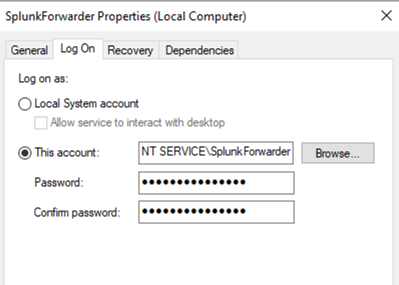
Instead of having to manually install Microsoft Sysmon on each and every Windows server in your environment, it would be optimal to install Sysmon on Windows machines via the Deployment Server (to learn more about the deployment server, click here). You can still manually install Sysmon, but that would be an exhaustive and time-consuming task if your environment contains tons of Windows servers.
The Sysmon Deploy Add-on for Cyences App installs and updates Sysmon on Windows machines. Also, it updates the Sysmon config file if there are any changes made to the Sysmon file.
-
Use Sysmon Deploy Add-on for Cyences App to install Microsoft Sysmon on Windows machines.
-
Download the latest Add-on build file named TA-sysmon-deploy-for-cyences.tgz - https://github.com/CrossRealms/Splunk-App-Sysmon-deploy-for-Cyences-App/releases/
-
Extract the file under the deployment apps directory on the deployment server.
-
Create a server class in the deployment server and deploy this Add-on to the required Windows hosts.
-
From Cyences’ navigation bar, go to Settings > Sysmon Deploy Audit for Sysmon deployment, auditing, and reporting.
-
This will start forwarding the Sysmon events to the indexer(s). Lastly, create an index named
epintelin the indexer(s) in order to receive data.
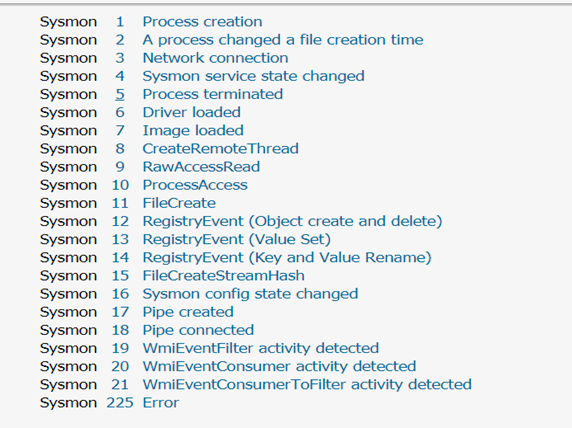
Note: The Sysmon Deploy Add-on for Cyences App generates auditing logs in index=_internal and actual Sysmon data in index=epintel. Sysmon collects several types of EventCodes from the Windows hosts. For the Cyences app, we will need to incorporate the following EventCodes: 1, 2, 5, 10, 11, and 25.
References
- https://docs.microsoft.com/en-us/sysinternals/downloads/sysmon
- https://docs.splunksecurityessentials.com/data-onboarding-guides/microsoft-sysmon/
Note: Sysmon data action field conflict detected, please look at Troubleshooting > Sysmon data action field issue section in the document to make sure your environment does not have the same issue.
Estimated Data Size
TODO