Fortinet FortiGate VPN Data
The Fortinet FortiGate Add-On for Splunk is required to collect firewall logs from FortiGate servers.
Splunkbase Download: https://splunkbase.splunk.com/app/2846/
Installation Guide: https://splunkbase.splunk.com/app/2846/#/details
How to Install and Configure the FortiGate Add-on:
-
Install the Add-on on the Heavy Forwarder.
- Configure the Add-on on the Heavy Forwarder.
- Getting data into Splunk Reference.
- Create an index named fortigate or update the macro definition in Cyences’ configuration page.
- Install the Add-on on the Search Head.
Note: Update the index value for VPN data macro definition in the Data Source Macros section in Cyences Configuration page.
FortiGate VPN Support and issue with action field extraction
-
Due to a field extraction issue in the Fortinet FortiGate Add-On for Splunk (field=action).
-
Verify that the FortiGate VPN data is supported by the Cyences App by following the instructions below.
How to fix the problem?
-
From Splunk’s navigation bar, go to Settings > Data models.
-
Search for the Authentication data model and click on it.
-
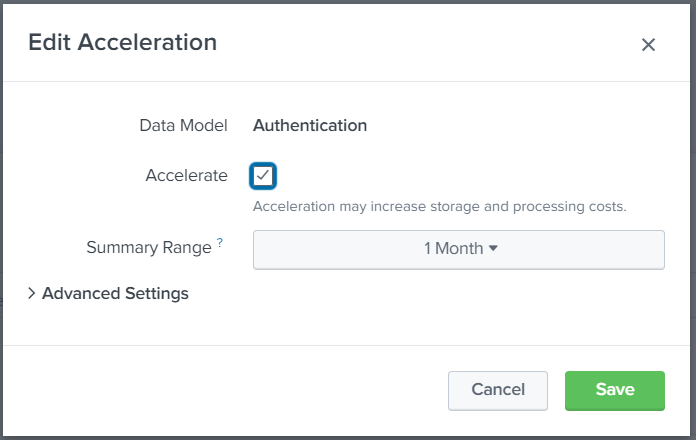
Click Edit > Edit Acceleration.
-
Uncheck the Acceleration box, then click Save.
-
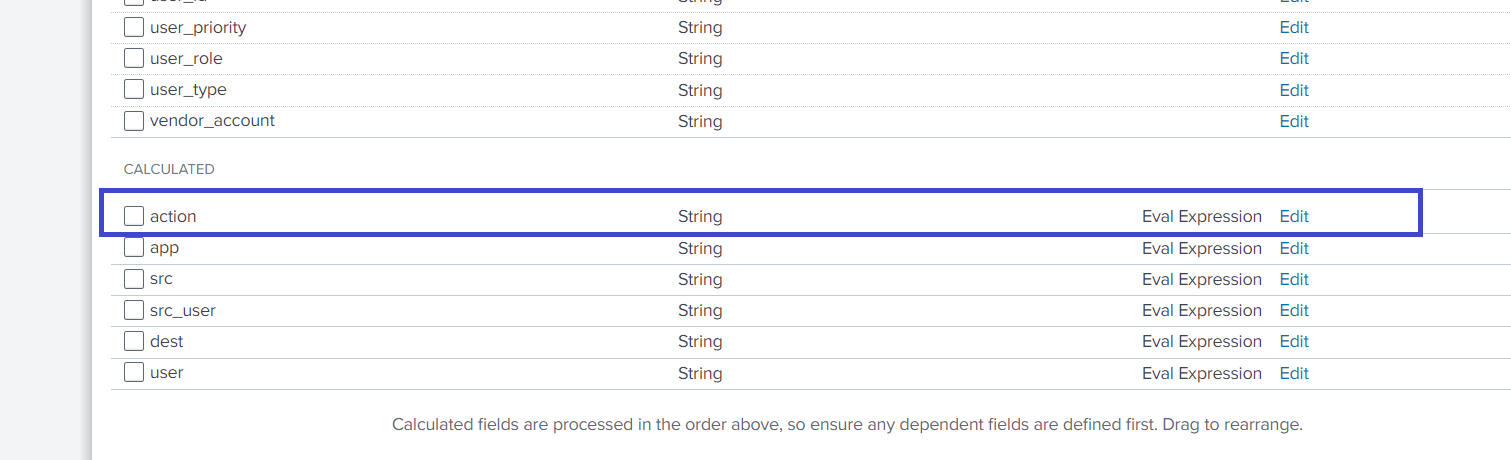
Under the Calculated fields section, click Edit for the action field.
-
Your current configuration should look similar to this:
if(isnull(action) OR action="","unknown",action) -
Replace the above configuration/eval expression with the contents below:
case(sourcetype="fgt_event" AND subtype="vpn" AND vendor_action IN ("tunnel-up", "phase2-up"), "success", sourcetype="fgt_event" AND subtype="vpn" AND vendor_action="ssl-login-fail", "failure", isnull(action) OR action="", "unknown", 1==1, action) -
Click Save.
-
Click Edit > Edit Acceleration.
-
Enable the Acceleration, then click Save.